
by USVBA Admin | Sep 29, 2022 | Cybersecurity, News
The cost of a data breach? Like all questions, the answer depends. For one thing it depends on the size of the business, for example for a US small business it is about $47,000 to $79,841. It is important to note that despite the relative low expense, a data breach...
by USVBA Admin | Sep 29, 2022 | Cybersecurity, News
As time has gone on, the awareness of cybersecurity threats has increased. By now, most people know someone who has had a brush with cybercriminals, or they too have been a victim of cybercrime. Unfortunately, this increase in cybersecurity awareness has been met...
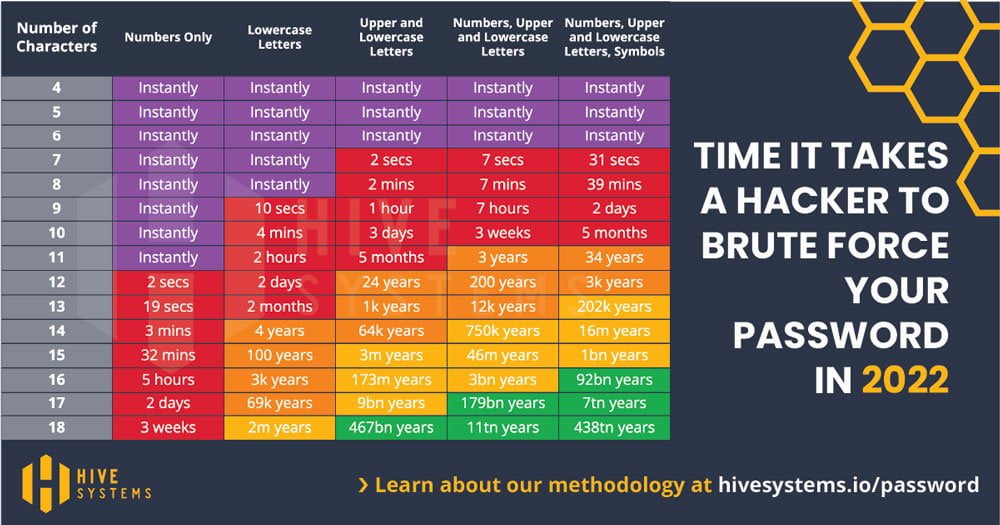
by USVBA Admin | Sep 29, 2022 | Cybersecurity, News
Passwords are what allow access to computers and systems; they are pretty much a necessary iterant to all users. They are the first line of defense in protecting systems and users. They are half of what is called the credentials. The first half is user...
by Tim Francis | Oct 21, 2021 | Cybersecurity, Sources Sought
SOURCE: GAO.GOV DATE: JUL 1, 2021 We testified about our work on the Department of Veterans Affairs’ efforts to modernize its health information and financial IT systems, address cybersecurity, and more. For example, although potential hurdles remain, VA made...
by admin | Apr 20, 2021 | Cybersecurity
Notice: The information in this report is a synopsis of the source articles. For in depth information please refer to the source cited at the end of each article. 171 Comply Cyber Alert Date: 20 April 2021 Title: Lazarus hacking group now hides payloads in...
by admin | Apr 6, 2021 | Cybersecurity
Highlight Your Resume with a Certificate! FPS Technical Data and Intellectual Property Certificate The FPS Technical Data and Intellectual Property Certificate program effectively blends detailed instruction with practical, hands-on exercises that are designed to...



